Berachain Operators - Stay Frosty with ValRewardAllocator ❄️
By James Lofgren, Protocol Specialist
In blockchain validation, security is paramount. Berachain’s Proof-of-Liquidity consensus relies on validators actively directing protocol rewards, but managing these rewards previously required frequent use of the operator key, increasing the risk of costly compromises. In August 2025, Berachain introduced the ValRewardAllocator role, allowing validators to delegate reward allocation tasks to a separate key while keeping the primary operator key offline. This update, detailed in BRIP-0004, marks a significant step toward more secure validator operations.
What Changed: Secure Delegation for Reward Management
The ValRewardAllocator role separates the responsibility of managing BGT (Berachain Governance Token) allocations from the operator key. Previously, validators had to use their operator key for every adjustment to the Cutting Board mechanism. Now, a designated address can handle these updates, authorized by the operator but executed independently.
This new functionality is implemented in the BeraChef contract, which governs reward distribution 0x4fad86f3ef82478db6cdbe70c43e8dd38390dcac. The key function is:
function setValRewardAllocator(
bytes calldata valPubkey,
address rewardAllocator
)
external
onlyOperator(valPubkey)
{
if (rewardAllocator == address(0)) {
ZeroAddress.selector.revertWith();
}
valRewardAllocator[valPubkey] = rewardAllocator;
emit ValRewardAllocatorSet(valPubkey, rewardAllocator);
}
This setValRewardAllocator function allows the operator to assign a reward allocator for a validator’s public key, protected by the onlyOperator modifier. Once set, the allocator manages reward adjustments without further operator key interaction.
Why This Matters: Mitigating Critical Risks
In Berachain, the operator key controls critical validator functions, but prior to the ValRewardAllocator role adjusting BGT allocations required signing with the operator key, increasing exposure risks. A compromised operator key could allow an attacker to:
- Replace the operator key with one under their control.
- Divert incentive rewards.
- Modify validator commission rates.
- Prevent recovery, as only the active operator key can authorize a replacement, forcing validators to exit entirely to regain control.
These vulnerabilities could result in digital asset losses and reputational damage. The ValRewardAllocator role addresses this by delegating reward allocation tasks to a separate key, significantly reducing the operator key’s exposure to potential risks.
Current Operator Key Management Practices
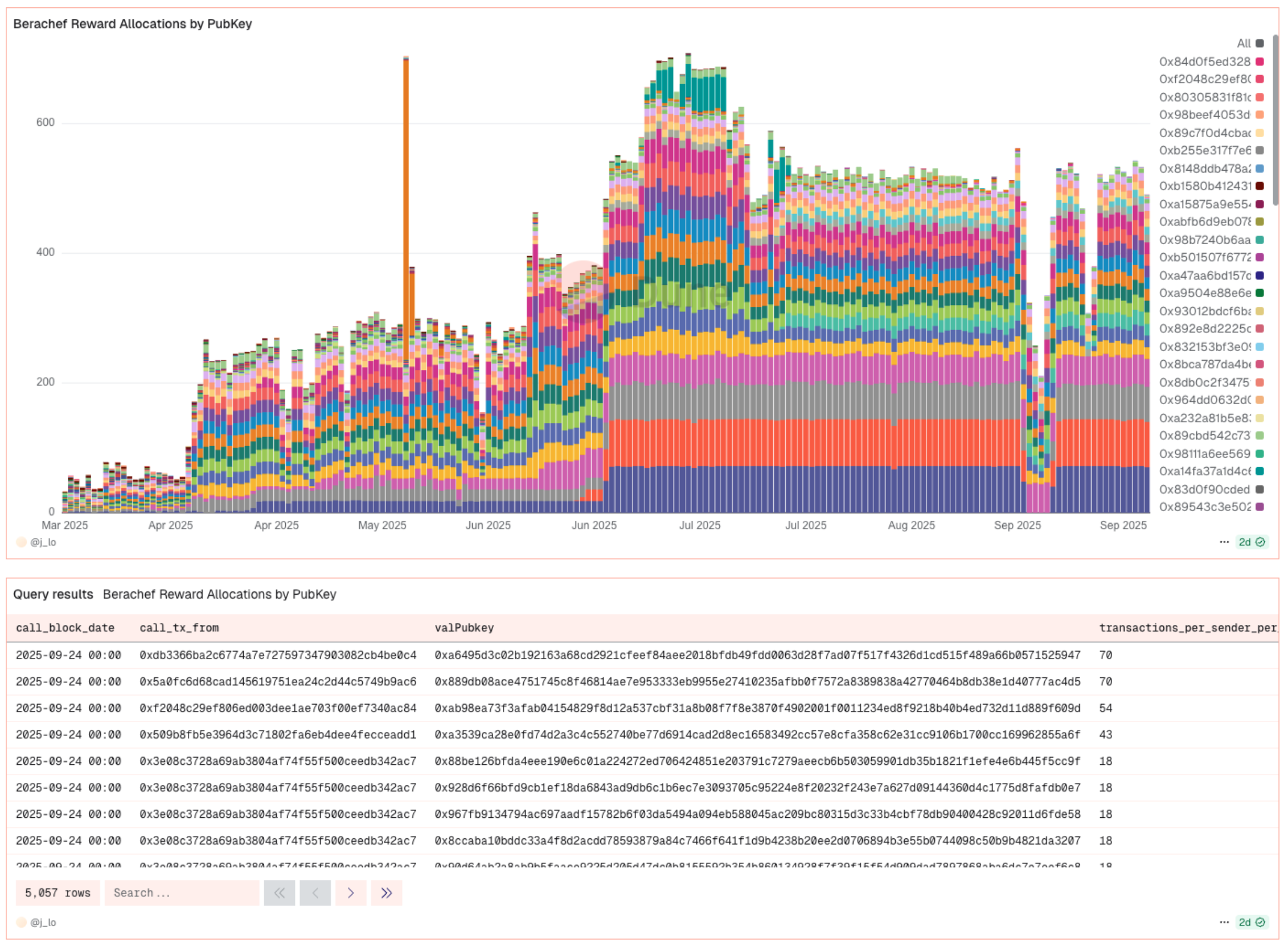
Without the ability to delegate the allocation function, operators had to balance efficiency with risk tolerance. This trade-off is evident in current practices, as shown by this Dune dashboard which provides insight into how different validators approach operator key management. The overwhelming majority of reward allocations appear to be validators with hot keys—private keys connected to the internet—running on scheduled services or cloud platforms, making them more vulnerable to attacks. Currently, 5 operator keys make up over 80% of daily reward allocation calls, with some exceeding 50 calls per day.
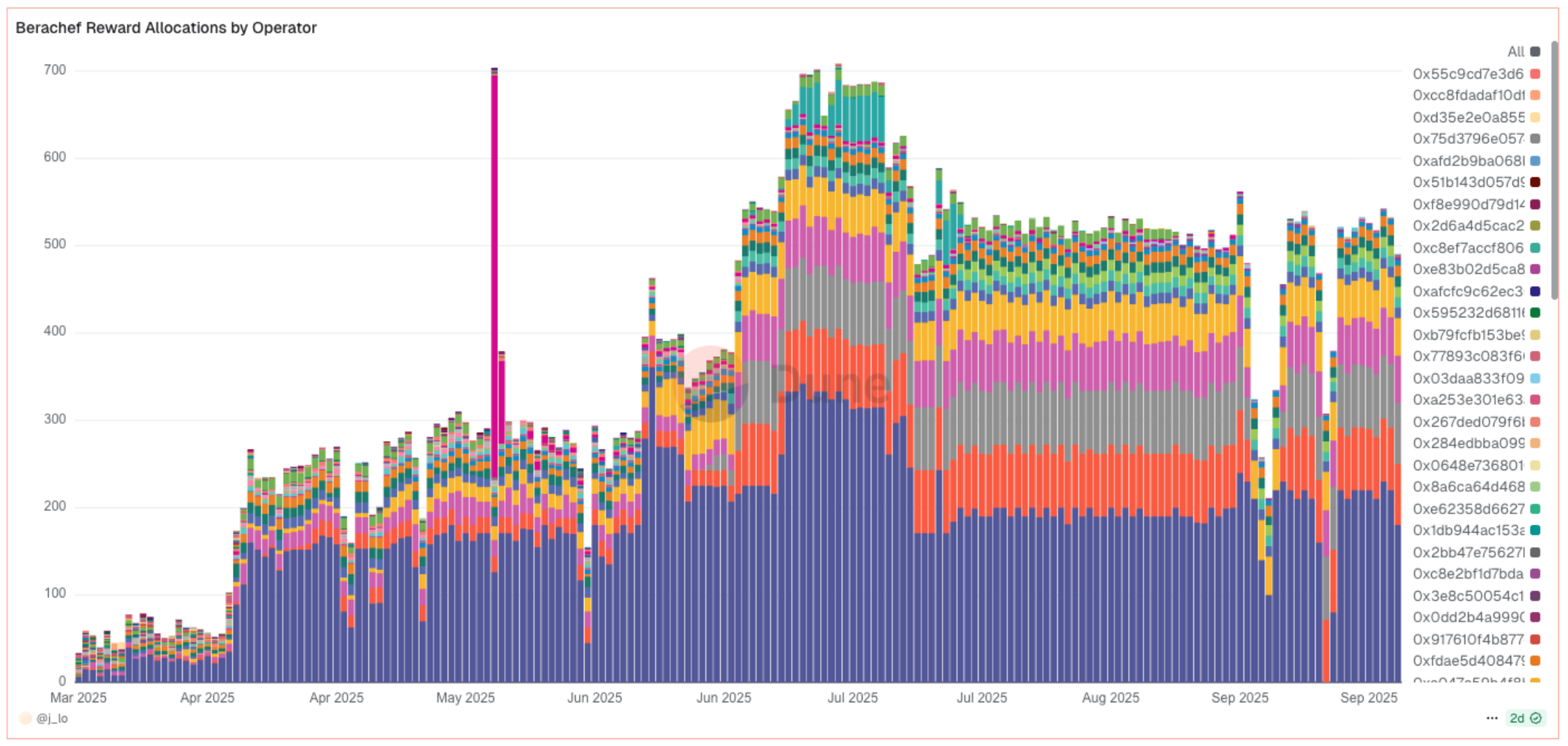
Looking deeper at the data, it appears two primary approaches exist:
-
Externally Owned Account (1:1): A single externally owned account (EOA) is tied to one validator public key. In a few observed cases, the operator key appears to be
hotbased on the frequency of reward allocation transactions. These setups often include recurring transfers of incentive rewards to secure assets, but the operator key remains online, increasing risk. -
Smart Contract Operator (1: Many): Custom setups, such as Infrared, manage multiple validators by setting the operator address to a proxy contract. This contract enables a permissioned hot key to be set (
0x3e08c3728a69ab3804af74f55f500ceedb342ac7) which is the only key that can call theQueueNewCuttingBoardfunction on the Infrared contract. The Infrared contract, which is set as the operator on multiple validators, then makes this call to the Berachef contract. This setup streamlines validator management, enforces strict access controls, and enables recovery if the hot key is compromised, while also supporting recurring asset sweeps. TheValRewardAllocatorrole now offers this functionality natively, eliminating the need for custom contract development.
The Opportunity: Security and Efficiency
The prevalence of operator hot keys underscores the need for safer practices. The ValRewardAllocator role presents a transformative opportunity for Berachain validators to enhance both security and efficiency. By delegating BGT allocation tasks to a separate key, validators can keep their operator key in secure cold storage, significantly reducing the risk of compromise while meeting the operational demands of frequent reward adjustments. With this update, validators can now adopt more secure practices without sacrificing efficiency, leveraging Berachain’s infrastructure to protect their assets and reputation.
Adoption Status: We’re Early
The ValRewardAllocator role, quietly introduced in August 2025, offers significant potential for enhancing validator security and efficiency, yet it remains untapped as validators take time to plan and implement this new feature. A Dune query tracking ValRewardsAllocatorSet events shows no transactions since launch as of this writing. This presents an opportunity for Berachain validators using hot keys to adopt more secure and efficient practices with this tool.
Future Integrations: Enabling Strategic Flexibility
Not only does the ValRewardAllocator role improve security, it also provides the foundation for future improvements such as BRIP-0005, which will utilize the ValRewardAllocator role to enable automated reward allocation strategies. Together, these tools allow validators to optimize allocations for delegates, enhancing efficiency without compromising on security.
As Berachain continues to make protocol improvements, adoption of these features is expected to grow. Validators should audit their key management practices, prioritize cold storage, and leverage delegation to minimize risks. The infrastructure is in place for validators to be more secure and efficient—now is the time!